I recently got fed up enough with ads while regularly using my mobile Android Marshmallow phone (/cough Youtube, App games, Reddit) that it pushed me to investigate a simple means of getting rid of them. The conditions were that it has to be easy to setup, maintain, and wouldn’t require rooting the phone.
So I began looking for solutions and recalled that Vultr recently started offering very cheap cloud instances at $2.50 USD a month with 1 CPU & 512 MB RAM. I also remembered hearing about Pi-hole and thought it would be the perfect mix! Initially, I had a Raspberry Pi 3 B collecting dust and thought I could’ve gone that route. However, I figured at the $2.50 price point was worth not having to have the Pi stored in the closet somewhere, always on, connected to the local network and jigger with local internal network settings. I concluded that the cloud solution would work perfectly.
I’m used to the smallest DigitalOcean or AWS instance I could find being in the area of $5 dollars a month. Which is why the cheapest Vultr instances caught my eye and I would rather have a dedicated instance just for this purpose, so as not to share space with any other instances running for other stuff.
Being new to Vultr, I signed up with a new account (affiliate link: Hey! more months of free adblocking if you find this useful).
They also had a “VULTRMATCH” promotion which doubles the credit for new accounts up to $100 match, so I ended up with $50 of credits which is good for 20 months of ad blocking on the cheapest instance.
(Edit 1: From reading the comments and after reading the promotion fine print, it appears that Credit is applied on a 50/50 basis, and will expire after 12 months. So if you’re looking for a year total of hosting for only this instance, $15 to then be doubled to $30 is the way to go. I’ll use my remaining balance on other projects instances, thanks Roque!)
Before launching the instance, use the “Looking Glass” links on https://www.vultr.com/faq/#downloadspeedtests page to check the nearest datacenters that have the lowest average ping time for your own IP, to improve latency when the ad blocking DNS requests go through.
4 packets transmitted, 4 received, 0% packet loss, time 3030ms rtt min/avg/max/mdev = 21.622/23.718/25.440/1.500 ms
Result will vary; Los Angeles Datacenter it was!
Being that the vanilla Ubuntu 16.04 LTS release is the Linux distro most familiar to me, that one was used to launch the instance. IPv6 & Private networking & Key-based auth were enabled, in case I want to hook into this project instance in the future.
The Hostname & Label fields used were just ones of a domain I had laying around unused, collecting Internet dust. Vultr also has a DNS service on their web panel. It could be used to host NS and set the custom A & CNAME records from there, so my unused domains were also set to them. (The lowest TTL for the CNAME, A, NS record cache seems to be 120 seconds.)
Let’s get to the steps for installation:
1. Instance prep
After the instance is launched via the web panel, begin with the ssh’ing into it via root and running these commands for prepping it.
# SSH into the new instance # Switch it out to be your servers IP ssh [email protected] # Get the latest packages updates apt-get update # Install the latest packages # To get rid of the "67 packages can be updated." login notification apt-get dist-upgrade -y
Not exactly sure about Vultrs’ default Ubuntu install, but to future-and-less-maintenance-proof the server even more, tutorials like https://help.ubuntu.com/community/AutomaticSecurityUpdates could be used to have the instance automatically receive updates. Not too concerned on future automatic updates breaking the application, as this will just be used for the ad-blocking project, not anything mission-critical.
1a. Creating Users
Just so the pi-hole application doesn’t get set up under root, we also need to create a user, just for it to run under.
adduser dnshole # Put in a randomly generated password # After dnshole user is created, allow sudo access to new user visudo # Then appended the dnshole line only, right below the root one. # So it looks like this below # User privilege specification root ALL=(ALL:ALL) ALL dnshole ALL=(ALL:ALL) ALL
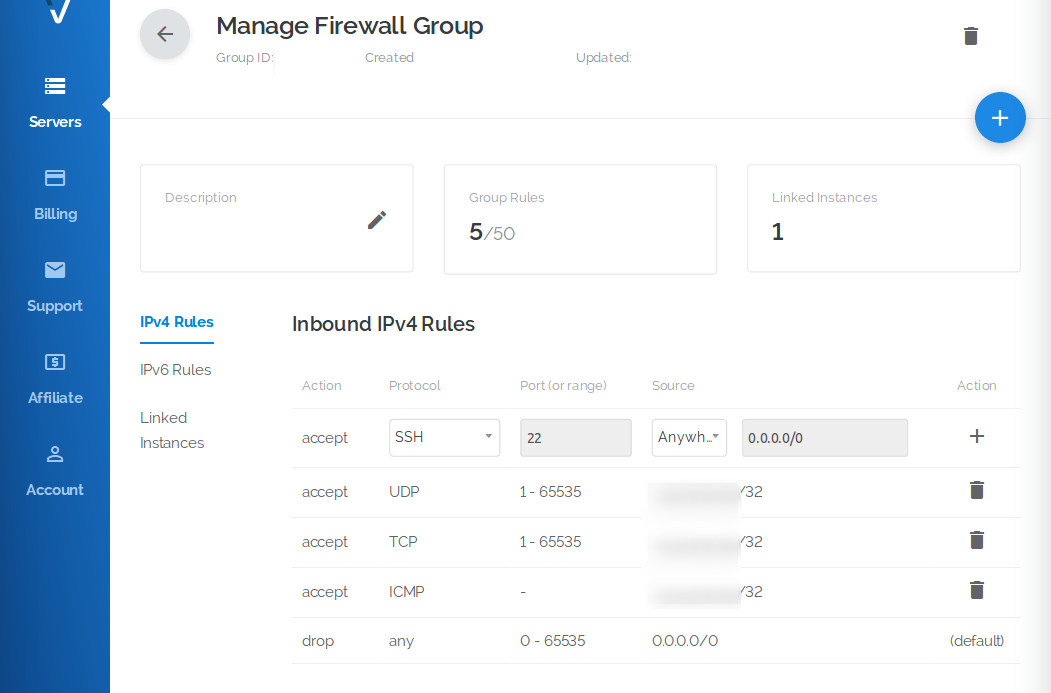
Vultr also has a firewall web portal on their web panel, that could be used to setup whitelisting rules for the purpose of only your IP being allowed to access the droplet. It secures down the instance even further and saves time from fudging around with Ubuntu’s internal ufw firewall tool, which contains the possibility of locking yourself out, if the ufw rules are messed up.
2. Installing Pi-Hole
After the custom non-root user is created, move on to getting Pi-Hole installed. I’m not one to pipe anything into bash without inspecting it, like they have listed for their installation. So I manually downloaded the file, inspected it, then piped it to bash from the local file.
# If you're still root # Change your user to emulate running shell as dnshole user sudo -u dnshole -s -H # change directories into dnsuser's homedir cd ~/ # Download pi-hole from master github repo curl -O "https://raw.githubusercontent.com/pi-hole/pi-hole/master/automated%20install/basic-install.sh" # View the file, that should have placed it into the current directory ll basic-install.sh -rw-r--r-- 1 dnshole dnshole 46743 Mar 10 23:16 basic-install.sh # Inspect it to make sure it's the correct file # Then running pipping it into bash to execute the installer cat ./basic-install.sh | bash
It should ask you for the randomly generated dnshole users password to sudo, put that in, then it should take you through the installation steps, pressing <Enter> for the <Ok> acknowledgments.
There’s some options to use different public secondary DNS resolvers, I went with OpenDNS’s. Then selecting to configure to block: [*] IPv4 Block ads over IPv4 and [*] IPv6 Block ads over IPv6 options accordingly. I didn’t have to manually enter any details, as it seemed to have autodetected the server’s IPv4 & IPv6 address. For the “Firewall in use” it has some default configurations it installs; those could also be used, but I used Vultr’s additional one on top:
It installed with no hiccups and I was provided with the details, which I copied to store later locally:
┌───────────────┤ Installation Complete! ├────────────────┐ │ │ │ Configure your devices to use the Pi-hole as their DNS │ │ server as their DNS server using: │ │ using: │ │ │ │ IPv4: 111.222.333.444 │ │ IPv6: 2001:0db8:85a3:0000:0000:8a2e:0370:7334 │ │ │ │ If you set a new IP address, you should restart the Pi. │ │ │ │ The install log is in /etc/pihole. │ │ │ │ View the web interface at http://pi.hole/admin or │ │ http://111.222.333.444/admin │ │ │ │ Your Admin Webpage login password is RANDomTXT │ │ │ │ <Ok> │ │ │ └─────────────────────────────────────────────────────────┘
- IPv4 / IPv6 address and passwords will be different for you.
I confirmed the server itself was working with running dig locally for a known ad network URL:
# Change the IP to be the public one of the Vultr instance dig -t a +short doubleclick.net @111.222.333.444 111.222.333.444
If the response A record of the command is the instance’s own IP, then that means it’s correctly intercepting it. When it intercepts a known ad host DNS record, it will show a “Website Blocked” HTTP/1.1 200 OK with the message. (I was reading that there’s some public repo’s that could be used to replace the page to customize it, if wanted.)
3. Configuring Android
Now that the instance is setup and working. The phone’s DNS network settings has to be setup to use it for the DNS name resolver to finally block ads.
All help-articles online advise viewing the Android Wifi network setting the phone is connected to, then configuring it to use DNS1 setting as the defined one with the example settings below, which never worked for me.
Upon selecting "Manage network settings" for the local wifi network: ☑️ Show advanced options IP Settings - Static ▼ - IP address: 192.168.1.103 (Your phones local IP on the network) - Gateway: 192.168.1.1 (You phones local gateway) - Network prefix length: 24 - DNS 1: Set the Ubuntu instances public IP address. - DNS 2: (empty) - Proxy: None
This seemed to be the hardest step, due to it not initially working when attempting it. It may work for you, but in viewing the Pi-Hole web panel after logging in, MAIN NAVIGATION >> Tools >> Tail pihole.log page wasn’t scrolling when attempting to browse apps on the phone.
I wasn’t going to go on a journey to root the phone for it to work. So I ended up having to download and install the DNS Changer app, then configured it to use the instance’s public IP address as the “DNS 1” option. Then I used OpenDNS as the second “DNS 2” option, as the field was required and clicked on Start. The app appears to create a VPN tunnel to work in setting up the DNS resolver correctly. I received the warning, and acknowledged it.
If you have better recommendations for getting it to work without an app, I’d be open to hear and will update this post. But everything online led to Android falling back to use Googles default 8.8.8.8 DNS resolvers, regardless and overriding any custom setup options in the phone’s network settings.
Conclusion
A weekend in, so far it has been good to see a lot less ads on the mobile apps. With Youtube, the ad at the beginning of videos seem to sometimes still pop up, but I haven’t noticed the ad that plays in-between the video yet. The video history also seems to have stopped, but I’m fine with giving up video history in exchange for ads.
If any issues arise, those take some debug-time to figure out. Regardless, I hope this helped with the basic setup!
Edit 1: Hacker News comments: https://news.ycombinator.com/item?id=13852109
Great DIY approach. I think Google now offers free instances, and there’s an Android app called Adguard offering a VPN strategy for $10 a year.
This is great! I have a $2.50 Vultr that I was testing, but now I will use it for this purpose. Thanks!
That Vultr credit will expire after a year. Of that $2.50 charged every month half comes off the cash balance and half off the credit balance. So use the rest of the $35 credit in other projects. Pi hole is great.
Thanks Roque, edited post to reflect the promotion details. Good to know!
Wait, does this mean you can set up a VPN on a DO server for Netflix outside of the US purposes?
No, it only acts as a DNS resolver like OpenDNS or Google’s public DNS.
So it would just affect when the DNS queries go to known ad sites, in which they would be blocked. Proxying through Netflix would be a vpn proxy tunnel which pipes all traffic through the proxy, unrelated to DNS queries here.
Imagine if you spent that $30 a year in paying app developers for their ad free version so that they can eat.
Why not just root your phone and replace the hosts file one that blocks a lot of the add networks, for example the one that pi-hole uses. There is even an app in the xposed framswork that does this. Seems like an expensive way to block adds.
Can someone tells me the est. bandwidth traffic per month on such setup?
For EU geeks… You can go lower than 2.5$ Try this:
https://www.arubacloud.com/vps/virtual-private-server-range.aspx